What Is The Best Ldap Service For Securing Mds Data
Active Directory (Advertizing) is one of the core pieces of Windows database environments. It provides authorization and authentication for computers, users, and groups, to enforce security policies across Windows operating systems. LDAP, or Lightweight Directory Admission Protocol, is an integral part of how Active Directory functions. Understanding the role LDAP plays in the functioning of Advertizement is essential to protecting your business from critical security issues.
This guide will define LDAP in the context of Agile Directory, explain the importance of both for security, and gear up out best practices to follow when using AD, including the implementation of a monitoring and management tool like SolarWinds® Access Rights Managing director (ARM).
What Is Active Directory LDAP?
Lightweight Directory Admission Protocol (LDAP) is an application protocol for working with various directory services. In other words, while information technology's supported past Active Directory, it's also used with other services.
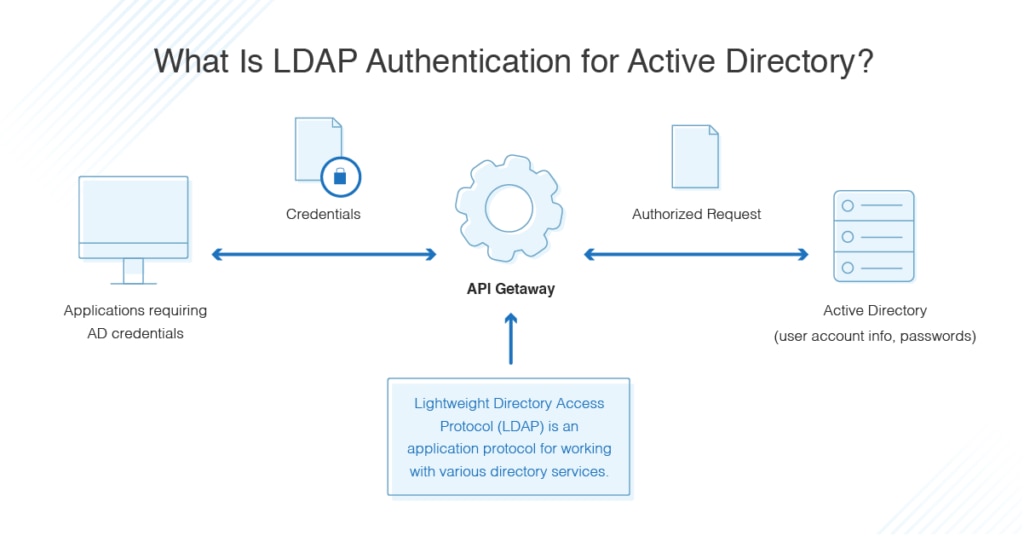
Directory services, such equally Active Directory, store user and account information, and security information like passwords, and and so let the data to be shared with other devices on the network. LDAP is the language applications apply to communicate with other servers also providing directory services. It'southward essentially a mode to "talk" to Agile Directory and transmit messages between AD and other parts of your IT environment.
The fashion yous brainstorm an LDAP session is past connecting to an LDAP server, known as a Directory System Agent, which "listens" for LDAP requests. "Domain controller" is another proper name for the server responsible for security hallmark requests. For users, domain control (DC) is the centerpiece of Active Directory. DC determines how Advertizing provides hallmark, stores user account information, and enforces the security policies you've applied beyond the domain controller or server.
How Does Active Directory Work With LDAP?
The next matter you need to understand is how AD LDAP authentication works. Substantially, you need to gear up LDAP to authenticate credentials against Active Directory. The "Demark" functioning is used to set the authentication state for an LDAP session in which the LDAP client connects to the server.
You have two options when it comes to performing LDAP authentication: simple and SASL.
- Simple authentication: This encompasses 3 possible approaches – anonymous authentication, unauthenticated authentication, and proper name/password authentication. In well-nigh cases, simple authentication essentially means a name and password are used to create a Demark request to the server for authentication.
- SASL authentication: The SASL (Simple Hallmark and Security Layer) framework uses another hallmark service—for example, Kerberos—to binds to the LDAP server, so uses the authentication service to cosign. This can provide enhanced security, every bit the separation of authentication methods from application protocols makes the directory less vulnerable in general.
By default, all LDAP authentication messages are sent in plain text, which can leave LDAP authentication processes open up to security problems. To prevent this, you should be using a security measure such as encryption using TLS, or Transport Layer Security.
One time you lot have chosen your LDAP authentication method and accept completed the procedure of LDAP integration with Agile Directory, you tin utilise the combination of these two systems with whatever application y'all want. This means y'all tin use Active Directory to manage permissions for your application, files, groups, then on, with LDAP as the messenger helping Advertisement to integrate with the rest of your systems.
Brand sure your Active Directory LDAP configuration settings are accurate at all times. This entails knowing whether hallmark is enabled, whether you're using simple or SASL authentication, whether authentication for FTP access is enabled, and whether user and group synchronization is enabled. Another cistron you might want to consider is how your queries and search bases are gear up; otherwise, you might be missing users and groups in the grade of processes like scanning for security issues or performing checks prior to audits.
Why Are LDAP and Agile Directory Important?
For managed services providers, it might be obvious why LDAP and Active Directory are and so of import, but if yous're new to this space, hither's why yous demand to think carefully about how to use them effectively.
Active Directory is office of the security layer for your Information technology systems, and LDAP is a cadre part of how AD works. This means both pieces are critical for keeping your It environment secure.
Active Directory is the role of your system designed to provide a directory service for user management. Information technology helps y'all manage and command all the devices on your network, including computers, printers, services, and mobile devices, and the users who engage with the devices. You can assign privileges to each user or group of users to allow them admission to the objects (devices) or information independent in Active Directory.
Active Directory authentication is important because access to data in the directory can make or break system security, and directory services are essentially a phonebook for everything your organisation holds in terms of information and devices.
The directory server and server LDAP integration are a critical result of these services functioning appropriately and securely. With LDAP, users can admission the information they need in AD to exercise their jobs finer. To configure LDAP correctly, you need to sympathize what hallmark processes you need, how users will be searching the systems, and where your security and information needs prevarication.
Due to the critical part of Active Directory in your It environment, it can be a target for hackers and malicious actors who want to breach your security systems. If a single loftier-level or high-admission account is accessed, you risk the exposure of sensitive data such as files and information, or passwords for other accounts. LDAP is key to protection in Agile Directory because it provides the authentication piece of the whole operation.
Active Directory All-time Practices
Active Directory plays a vital office in the security systems of your IT surround. For this reason, when using AD, take intendance to adhere to the following all-time practices, for more details read our Ultimate Guide to Agile Directory Best Practices:
- Ensure proper configuration. Take the configuration steps slowly and carefully, to make sure Active Directory is set upward right in the first place. With proper configuration of your LDAP servers, yous'll cut down on the likelihood of an Ad problem impacting your finish users.
- Carefully configure AD groups . When setting up your Active Directory groups, exist sure to separate them based on role or the admission they should accept and keep these groups up to date. For example, if someone moves into a new role, their group designation should be updated. Managing these aspects of Advertizement helps to preclude unauthorized admission, so your arrangement stays secure.
- Follow the principle of to the lowest degree access. When it comes to Active Directory, setting upwards each user or group with the least access necessary to do their chore or execute their function is of import. The more access whatever one group or user has, the higher the chance the access can be driveling. In other words, the less access you requite each user and group, the safer you proceed your systems as a whole.
- Make use of tools. One of import step you can have to make sure your Active Directory is gear up correctly is to utilise loftier-quality professional tools. A centralized solution like SolarWinds Access Rights Managing director volition help you to effectively manage your Active Directory configurations and permissions.
ARM includes several features specifically designed for managing Active Directory, including tools to simplify Agile Directory delegation, tools for group management, and permissions reporting. Additionally, the Active Directory Auditing Tool helps ensure security and compliance. These features make certain your AD setup is both secure and efficient.
Whether you choose ARM or another tool, it's vital you lot examination information technology thoroughly in a portion of your business environs before rolling it out to your entire IT system. SolarWinds allows you lot to practice this past downloading a thirty-day free trial of ARM.
In add-on, perform regular updates, generate Agile Directory permissions reports, and check to ensure your software and tools are upwardly to appointment and working finer for your concern. - Undertake regular reviews. Along the same lines, you should also be performing regular reviews of your Active Directory and LDAP hallmark setup, regardless of whether you're using a tool or not. You demand to ensure there are no configuration changes capable of creating a security risk or an error.
Managing LDAP and Active Directory
LDAP is a critical part of the functioning of Active Directory, as it communicates all the messages betwixt Ad and the residuum of your Information technology surround. For this reason, implementing the correct configuration and hallmark settings is vital to both the security and the day-to-day performance of your IT systems. Past following the above processes, including adopting a tool similar SolarWinds ARM to monitor and manage your Advertizing user access rights, yous can make sure your Active Directory is set up correctly with LDAP authentication, and you're using it in a secure and efficient mode.
What Is The Best Ldap Service For Securing Mds Data,
Source: https://www.dnsstuff.com/active-directory-ldap-authentication
Posted by: naranjonintiost.blogspot.com


0 Response to "What Is The Best Ldap Service For Securing Mds Data"
Post a Comment